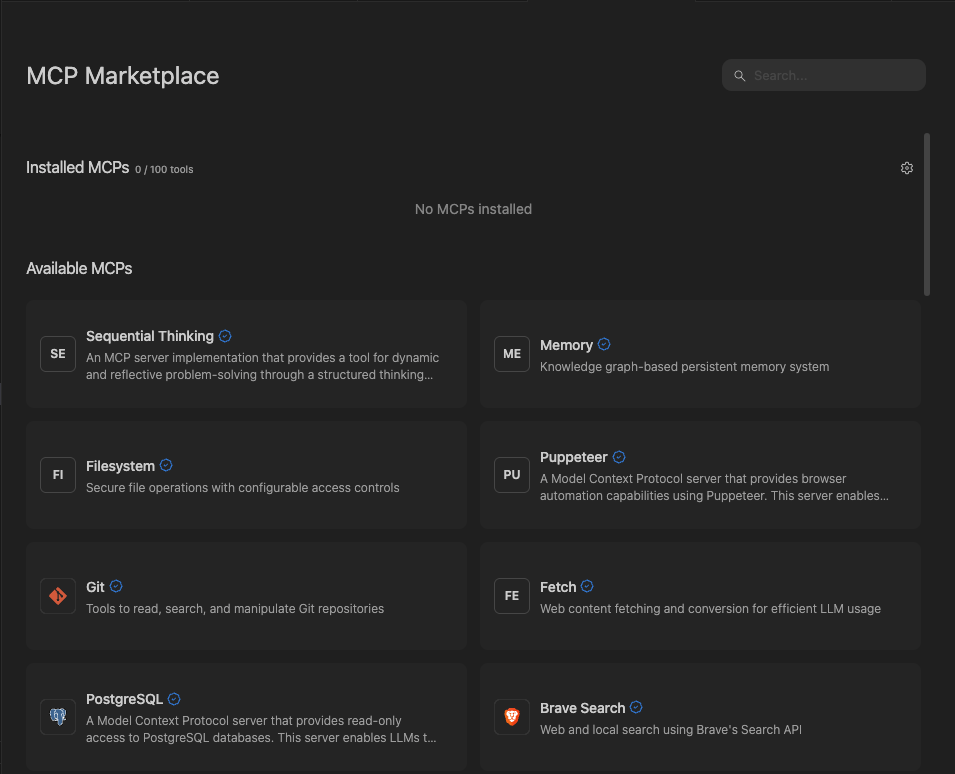
Adding a new MCP
New MCPs can be added from the MCP Marketplace, which you access by clicking on theMCPs icon in the top right menu in the Cascade panel, or from
the Windsurf Settings > Cascade > MCP Servers section.
If you cannot find your desired MCP, you can add it manually by editing the raw mcp_config.json file.
Official MCPs will show up with a blue checkmark, indicating that they are made by the parent service company.
When you click on a MCP, simply click Install to expose the server and its tools to Cascade.
Windsurf supports three transport types for MCP
servers: stdio, Streamable HTTP, and SSE.
Windsurf also supports OAuth for each transport type.
For http servers, the URL should reflect that of the endpoint and resemble https://<your-server-url>/mcp.
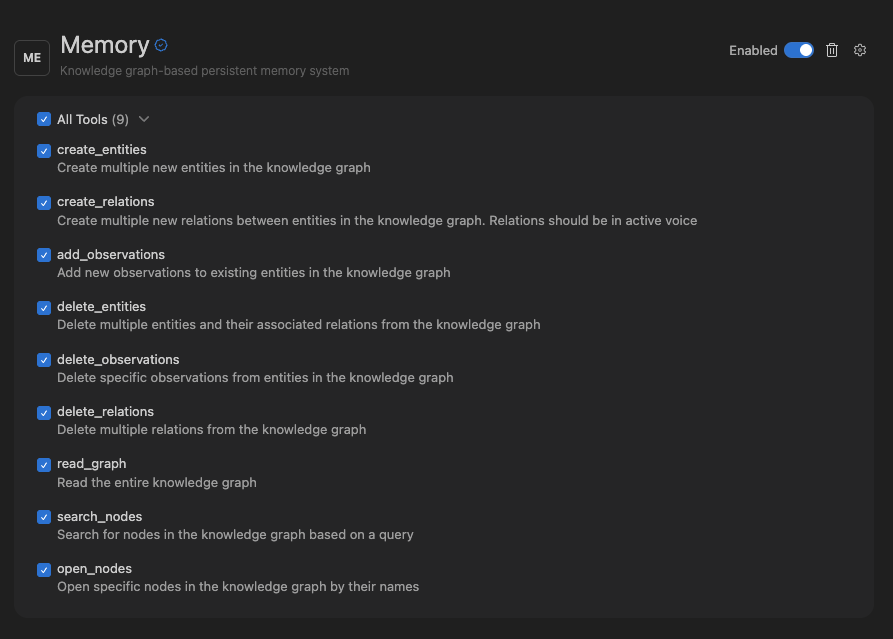
Configuring MCP tools
Each MCP has a certain number of tools it has access to. Cascade has a limit of 100 total tools that it has access to at any given time. On each MCP settings page, you can toggle the tools that you wish to enable. To open settings for a MCP, click on theMCPs icon in the top right menu in the
Cascade panel, and click on the desired MCP.
mcp_config.json
The~/.codeium/windsurf/mcp_config.json file is a JSON file that contains a list of servers that Cascade can connect to.
Here’s an example configuration, which sets up a single server for GitHub:
Popular MCP Server Examples
Below are configuration examples for some commonly used MCP servers. These can be added to yourmcp_config.json file.
GitHub
Repository management, file operations, and GitHub API integration.
GitHub
Repository management, file operations, and GitHub API integration.
Slack
Channel management and messaging capabilities for Slack workspaces.
Slack
Channel management and messaging capabilities for Slack workspaces.
- Create a Slack App at api.slack.com/apps
- Add the required OAuth scopes (e.g.,
channels:read,chat:write,users:read) - Install the app to your workspace and copy the Bot User OAuth Token
PostgreSQL
Read-only database access with schema inspection capabilities.
PostgreSQL
Read-only database access with schema inspection capabilities.
Filesystem
Secure file operations with configurable access controls.
Filesystem
Secure file operations with configurable access controls.
Brave Search
Web and local search using Brave's Search API.
Brave Search
Web and local search using Brave's Search API.
Memory
Knowledge graph-based persistent memory system.
Memory
Knowledge graph-based persistent memory system.
Remote HTTP MCPs
It’s important to note that for remote HTTP MCPs, the configuration is slightly different and requires aserverUrl or url field.
Here’s an example configuration for an HTTP server:
Config Interpolation
The~/.codeium/windsurf/mcp_config.json file handles interpolation of
environment variables in these fields: command, args, env, serverUrl, url, and
headers.
Here’s an example configuration, which uses an AUTH_TOKEN environment variable
in headers.
Admin Controls (Teams & Enterprises)
Team admins can toggle MCP access for their team, as well as whitelist approved MCP servers for their team to use:MCP Team Settings
mcp_config.json.How Server Matching Works
When you whitelist an MCP server, the system uses regex pattern matching with the following rules:- Full String Matching: All patterns are automatically anchored (wrapped with
^(?:pattern)$) to prevent partial matches - Command Field: Must match exactly or according to your regex pattern
- Arguments Array: Each argument is matched individually against its corresponding pattern
- Array Length: The number of arguments must match exactly between whitelist and user config
- Special Characters: Characters like
$,.,[,],(,)have special regex meaning and should be escaped with\if you want literal matching
Configuration Options
Option 1: Plugin Store Default (Recommended)
Leave the Server Config (JSON) field empty to allow the default configuration from the Windsurf MCP Plugin Store.
Option 1: Plugin Store Default (Recommended)
Leave the Server Config (JSON) field empty to allow the default configuration from the Windsurf MCP Plugin Store.
- Server ID:
github-mcp-server - Server Config (JSON): (leave empty)
mcp_config.json):Option 2: Exact Match Configuration
Provide the exact configuration that users must use. Users must match this configuration exactly.
Option 2: Exact Match Configuration
Provide the exact configuration that users must use. Users must match this configuration exactly.
- Server ID:
github-mcp-server - Server Config (JSON):
mcp_config.json):env section can have different values.Option 3: Flexible Regex Patterns
Use regex patterns to allow variations in user configurations while maintaining security controls.
Option 3: Flexible Regex Patterns
Use regex patterns to allow variations in user configurations while maintaining security controls.
- Server ID:
python-mcp-server - Server Config (JSON):
mcp_config.json):- The regex
/.*\\.pymatches any Python file path like/home/user/my_server.py - The regex
[0-9]+matches any numeric port like8080or3000 - Users can customize file paths and ports while admins ensure only Python scripts are executed
Common Regex Patterns
| Pattern | Matches | Example |
|---|---|---|
.* | Any string | /home/user/script.py |
[0-9]+ | Any number | 8080, 3000 |
[a-zA-Z0-9_]+ | Alphanumeric + underscore | api_key_123 |
\\$HOME | Literal $HOME | $HOME (not expanded) |
\\.py | Literal .py | script.py |
\\[cli\\] | Literal [cli] | mcp[cli] |
Notes
Admin Configuration Guidelines
- Environment Variables: The
envsection is not regex-matched and can be configured freely by users - Disabled Tools: The
disabledToolsarray is handled separately and not part of whitelist matching - Case Sensitivity: All matching is case-sensitive
- Error Handling: Invalid regex patterns will be logged and result in access denial
- Testing: Test your regex patterns carefully - overly restrictive patterns may block legitimate use cases
Troubleshooting
If users report that their MCP servers aren’t working after whitelisting:- Check Exact Matching: Ensure the whitelist pattern exactly matches the user’s configuration
- Verify Regex Escaping: Special characters may need escaping (e.g.,
\.for literal dots) - Review Logs: Invalid regex patterns are logged with warnings
- Test Patterns: Use a regex tester to verify your patterns work as expected